- Authentication: Powered by IAM services for user identity verification, multi-factor authentication, and session management.
- Authorization: Utilizes Cerbos for policy-driven, fine-grained access control.
- Scalability: Deployed on Kubernetes for high availability, fault tolerance, and scalability.
- Extensibility: Designed as a SaaS platform, supporting integrations with third-party services and APIs.
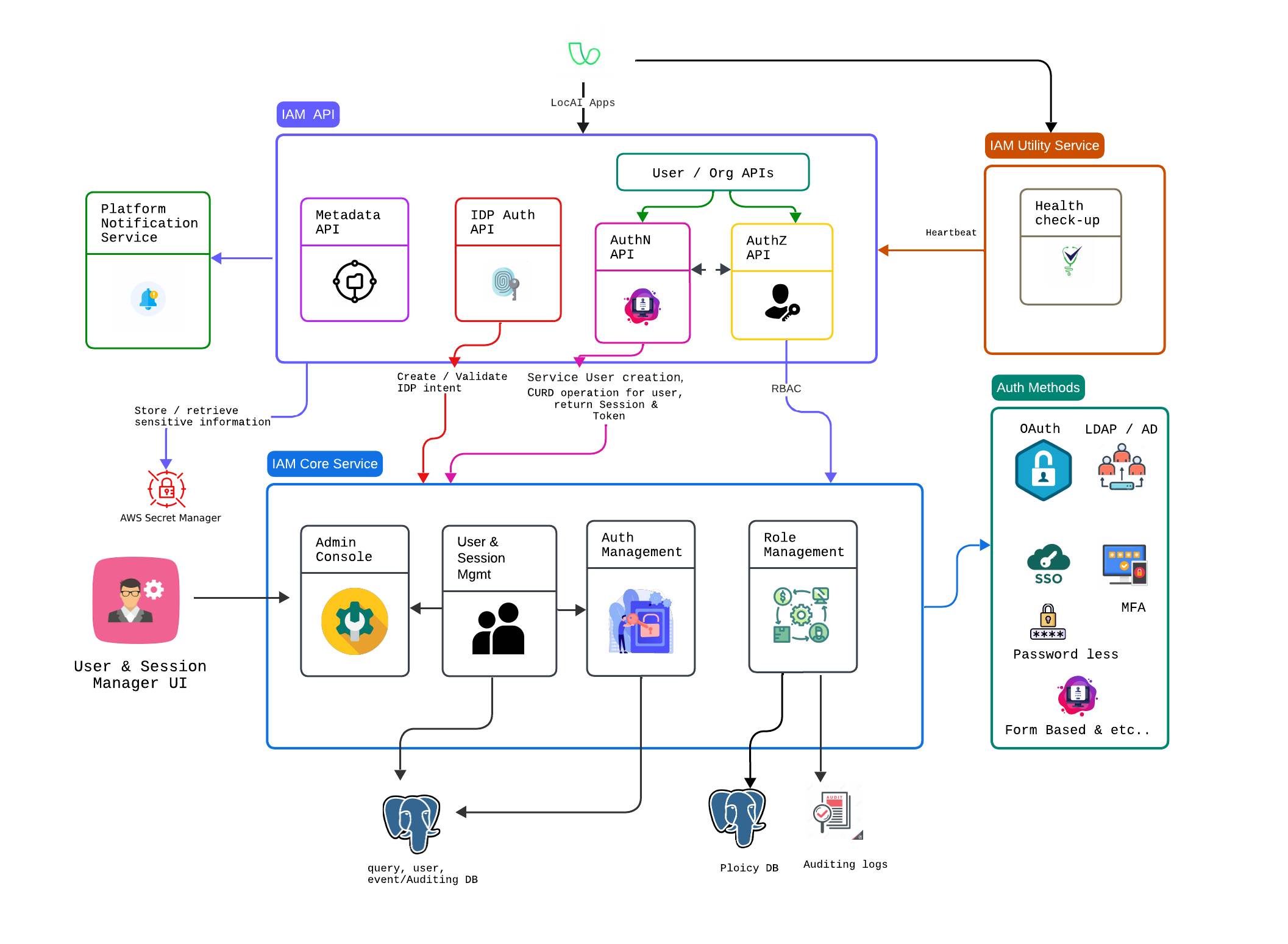
Platform - IAM Service System Architecture
Multitenancy Architecture
The IAM system is designed to support multi-tenancy, enabling secure and isolated management of identities and access across multiple tenants. Key architectural elements include:- Tenant Isolation: Logical data separation via database schemas or row-level security ensures secure and isolated tenant environments.
- Authentication: Supports tenant-specific authentication flows and identity provider configurations using IAM.
- Authorization: Leverages Cerbos for fine-grained, tenant-aware access control policies.
- Centralized Management: Admin portal enables onboarding, policy configuration, and usage monitoring for multiple tenants.
- Scalability: Kubernetes ensures horizontal scaling and high availability for diverse tenant workloads.
- Customizability: Tenants can customize workflows, branding, and access policies as per their needs.
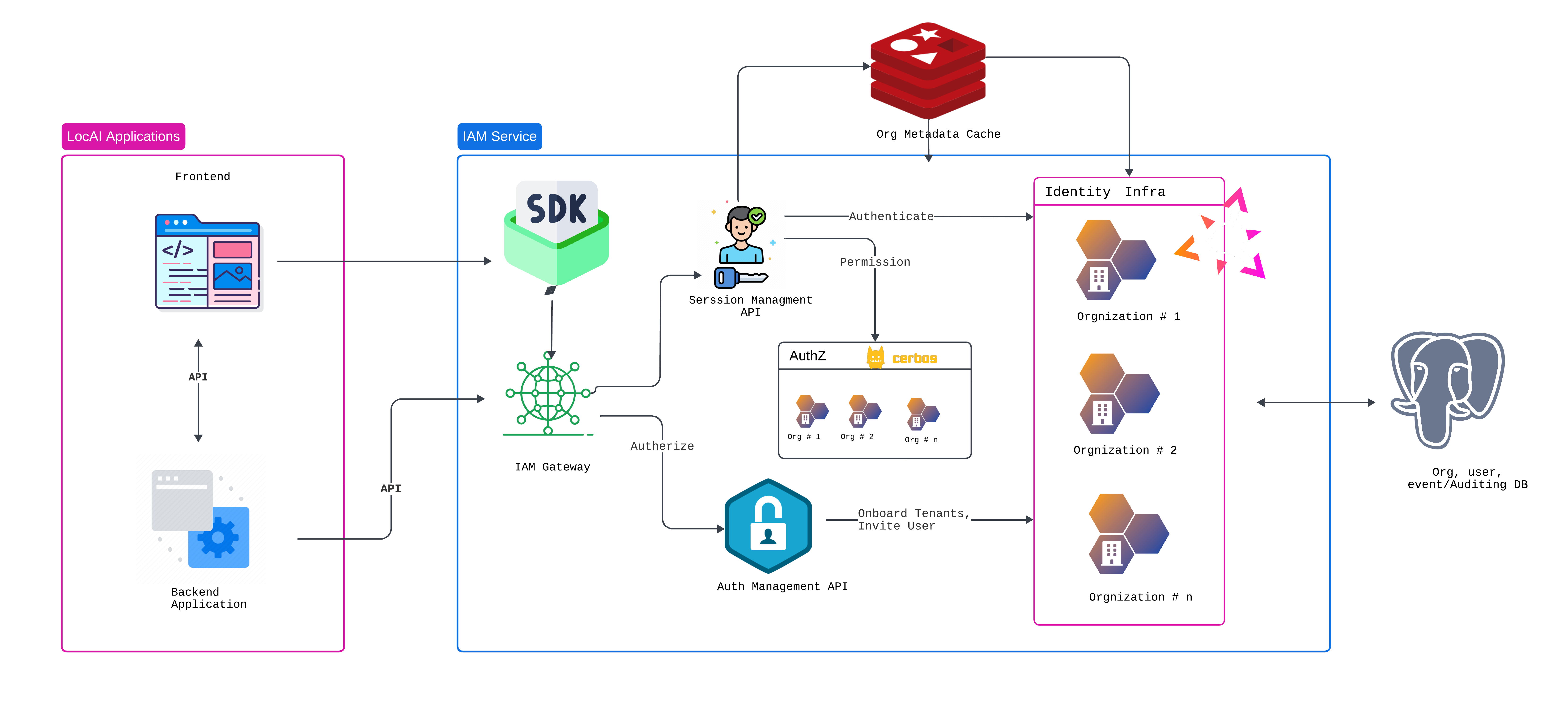
Multitenancy System Architecture
IAM Workflow
The IAM workflow ensures secure and efficient management of user identities, authentication, and access control within the platform. It is designed to streamline user operations while maintaining robust security and compliance.- User Onboarding: Facilitates user registration, profile creation, and initial role assignment.
- Authentication: Implements multi-factor authentication and single sign-on (SSO) using internal or third party services.
- Authorization:Enforces fine-grained access control policies via Cerbos, supporting role-based and attribute-based permissions.
- Session Management: Manages secure user sessions with token-based mechanisms for authentication and access continuity.
- Audit and Monitoring: Tracks user activities, access logs, and system events for compliance and security.
- User Offboarding:Ensures proper account deactivation or deletion, revoking roles and permissions as necessary.
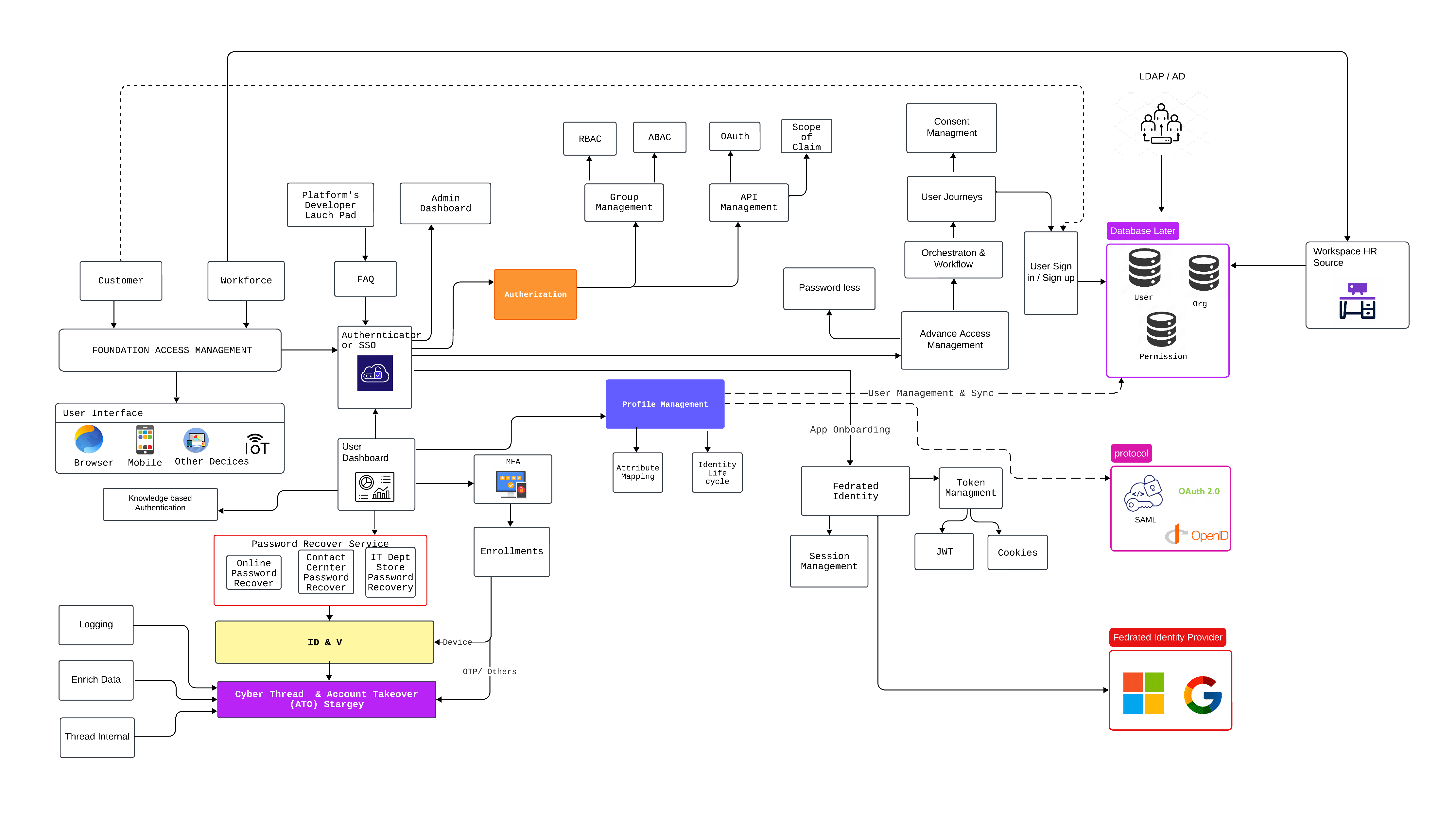
IAM Workflow

